Recent Major Attack: 143.45 ETH Lost
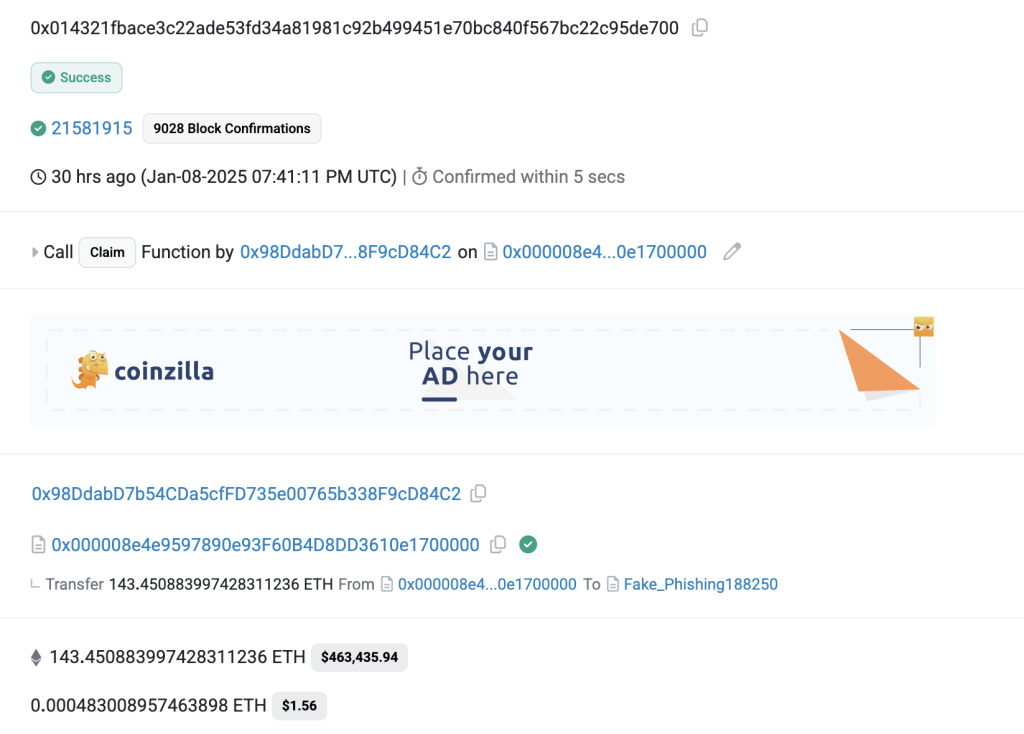
In a concerning development, a crypto user lost 143.45 ETH (approximately $460,895) through a sophisticated transaction simulation spoofing attack. This incident highlights a growing trend of attackers exploiting advanced features in modern Web3 wallets.
Understanding Transaction Simulation

Modern Web3 wallets incorporate transaction simulation as a user-friendly feature. This capability allows users to preview the expected outcome of their transactions before signing them. While designed to enhance transparency and user experience, attackers have found ways to exploit this mechanism.
The Exploitation Mechanism
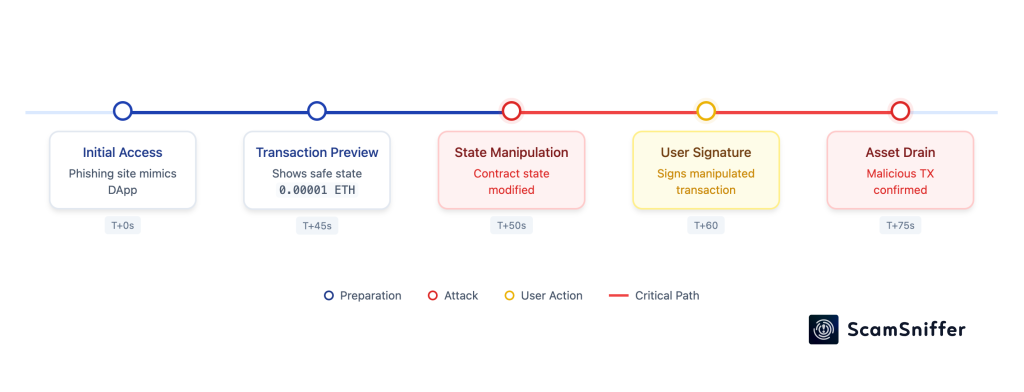
The core vulnerability lies in the time gap between transaction simulation and execution. Malicious actors have developed phishing sites that can manipulate on-chain states during this crucial window, leading to devastating results.
Attack Sequence Breakdown:
- Phishing site initiates what appears to be a simple “Claim” ETH transfer
- Wallet simulation shows a minimal ETH receipt (0.000…0001 ETH)
- Backend systems quietly modify the contract state
- The actual transaction executes, resulting in complete wallet drainage

Recent Attack Analysis
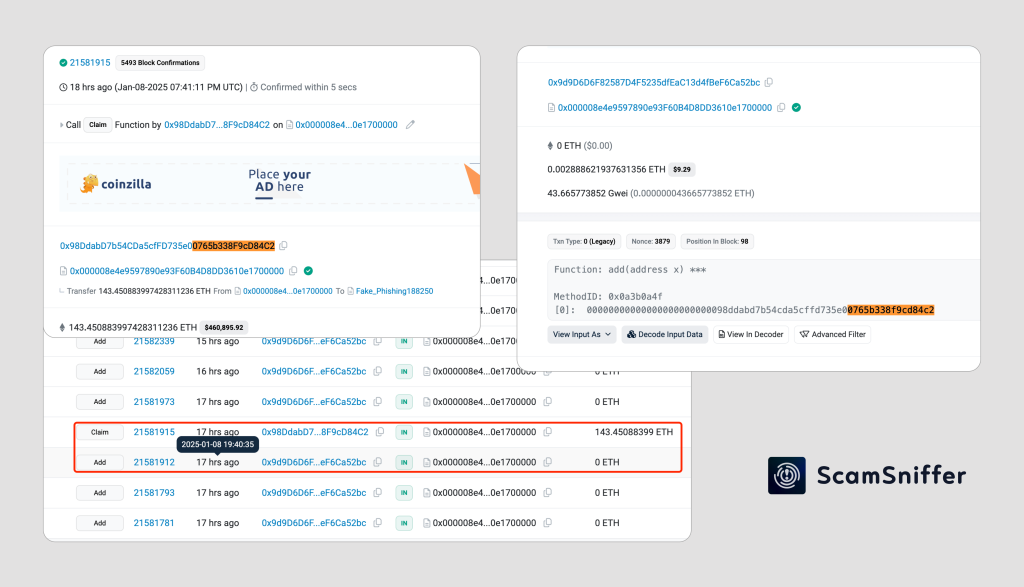
A detailed examination of the recent incident reveals:
- The phishing site modified the contract state strategically
- The victim signed the transaction approximately 30 seconds after the state change
- The “Claim” function executed as planned by the attackers
- The entire wallet was drained while appearing legitimate in simulation
Wallet Enhancement Suggestions
To better prevent such attacks, Web3 wallets should consider the following optimizations:
Real-time Simulation Refresh Mechanism
- Dynamically adjust simulation refresh rates based on different blockchain block times
- Force refresh simulation results before critical operations
- Display timestamps and block heights for simulation results to increase user awareness
- Add prominent expiration warnings for simulation results older than specific thresholds
Security Service Integration
- Integrate phishing contract blocklist from major security service providers
- Implement real-time security checks for interacting contract addresses
- Add prominent risk warnings for suspicious contracts
UI/UX Improvements
- Clearly display the time-sensitivity of simulation results
- Add additional confirmation steps for high-risk operations
- Provide more detailed transaction risk analysis information
- Simplify security alert presentations to improve user attention
Protection Guidelines
To protect yourself from these sophisticated attacks:
- Always double-check transaction details thoroughly
- Verify all contract interactions independently
- Maintain healthy skepticism toward “free claim” offers
- Stick to trusted and verified dApps
- Consider using security tools like ScamSniffer extension
Evolution of Phishing Attacks
This new attack vector represents a significant evolution in phishing techniques. Rather than relying on simple deception, attackers are now exploiting trusted wallet features that users rely on for security. This sophisticated approach makes detection particularly challenging.
Conclusion
The crypto community must remain vigilant as attack methods continue to evolve. Always verify transactions through multiple sources and never rush into signing transactions, regardless of how legitimate they may appear in simulation.
Stay safe and share this information to protect others in the Web3 community.
About ScamSniffer
ScamSniffer is a security platform focused on Web3 anti-scam, providing real-time anti-scam protection by combining off-chain and on-chain monitoring data.
Our browser security extension helps users identify phishing websites and suspicious transactions, providing comprehensive protection for Web3 users.
Our security solutions have been adopted by wallets including Binance, Bybit, OneKey, Phantom, TokenPocket, and others, protecting millions of Web3 users monthly from phishing and fraud threats.
We are committed to building a safer Web3 ecosystem for the next billion users.
